Single Sign-on (SSO) permits a user to use a set of login credentials set up in one Identity Provider (IdP) application to access Service Provider applications which significantly simplifies the login process. This feature is extremely useful for enterprise-level companies that use multiple software platforms on a daily basis and need better user-account management.
Kurtosys is an SSO provider which means users can log into the Kurtosys platform and Kurtosys portals using their credentials from other applications that use the common SAML 2.0 authentication protocol. This eliminates the need for users to set up and remember multiple passwords, thus reducing password fatigue and improving security.
For users to access the Kurtosys App using their Auth0 logins, follow the steps below. It’s a good idea to build the SSO Application in Auth0 and the Kurtosys Login Strategy concurrently as information from the one is needed in the other.
Setting up Auth0 as the Identity Provider (IdP)
- Log in to your Auth0 account.
- Click Applications.
- Click + Create Application.
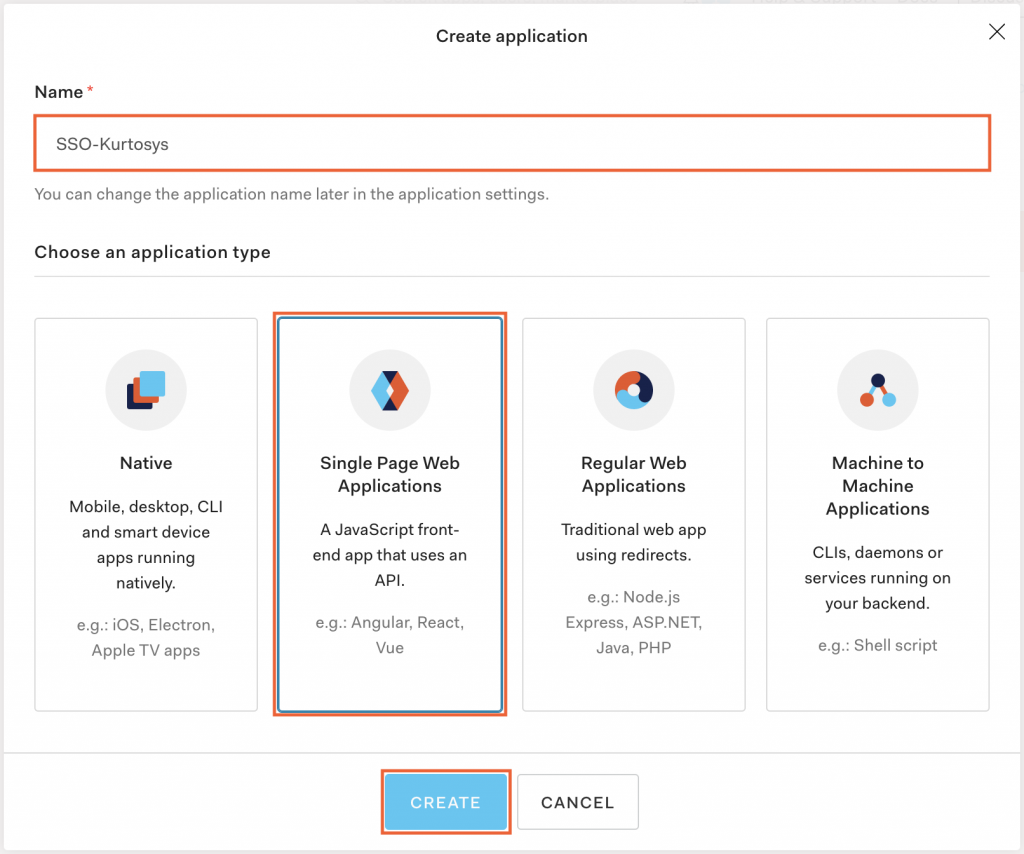
- Name the application, e.g. SSO-Kurtosys.
- Click Single Page Web Applications as the application type.
- Click CREATE.
- Click the Addons tab.
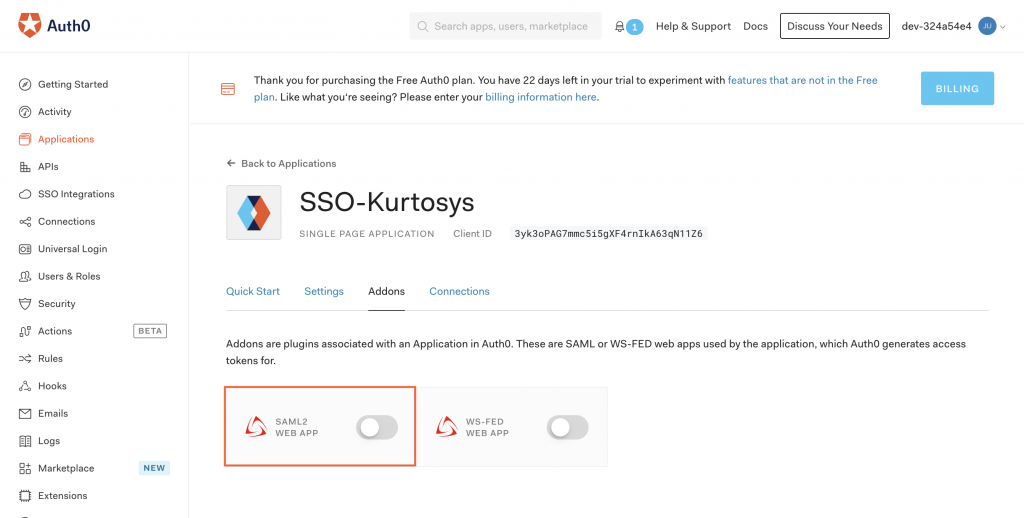
- Toggle on SAML2 WEB APP.
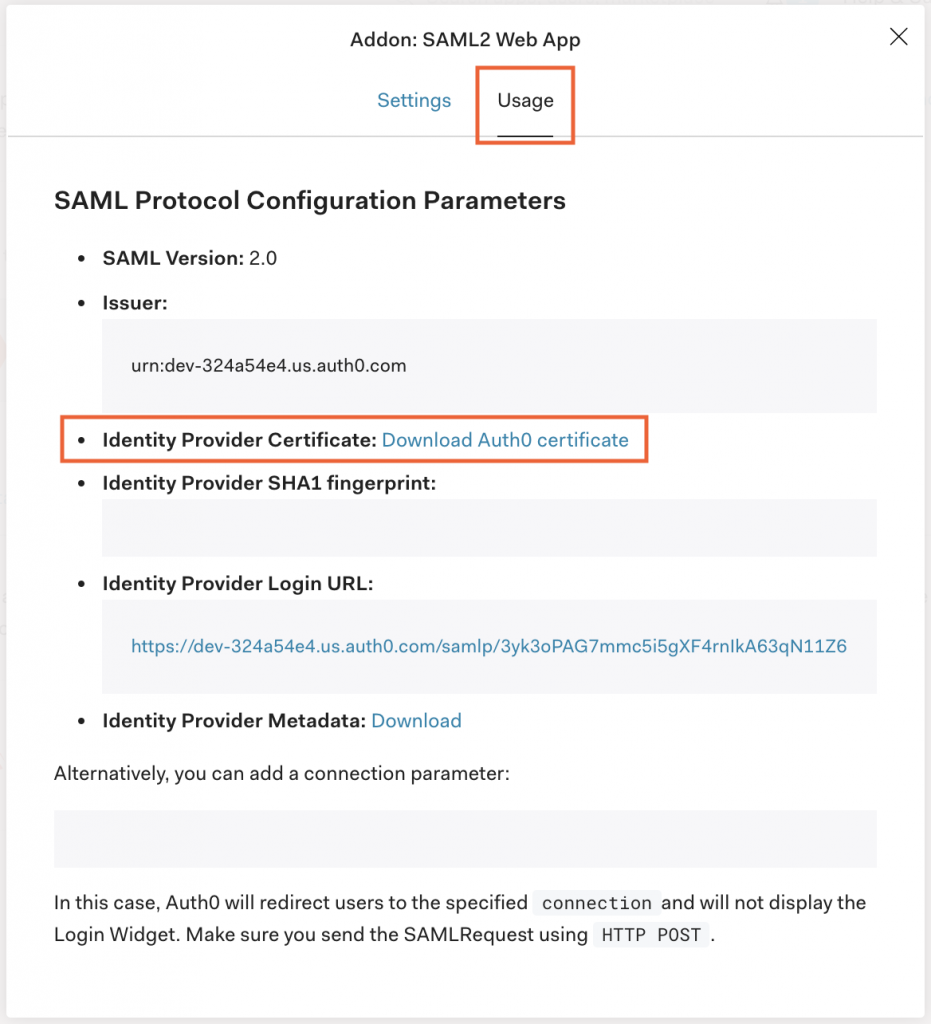
- Under the Usage tab, click Download Auth0 Certificate.
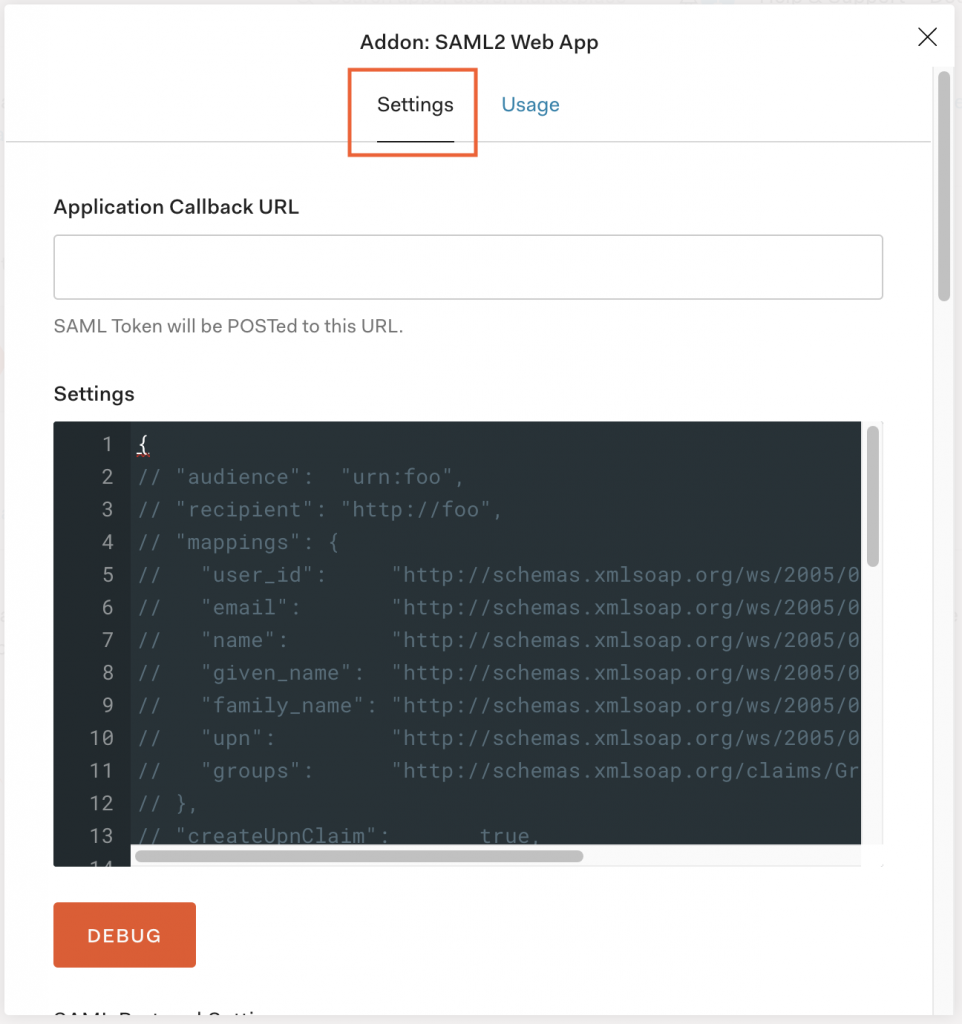
- Click the Settings tab.
Setting up Single Sign-On for Auth0 in Kurtosys App
- Click the System Administration cog.

- Click Authentication.
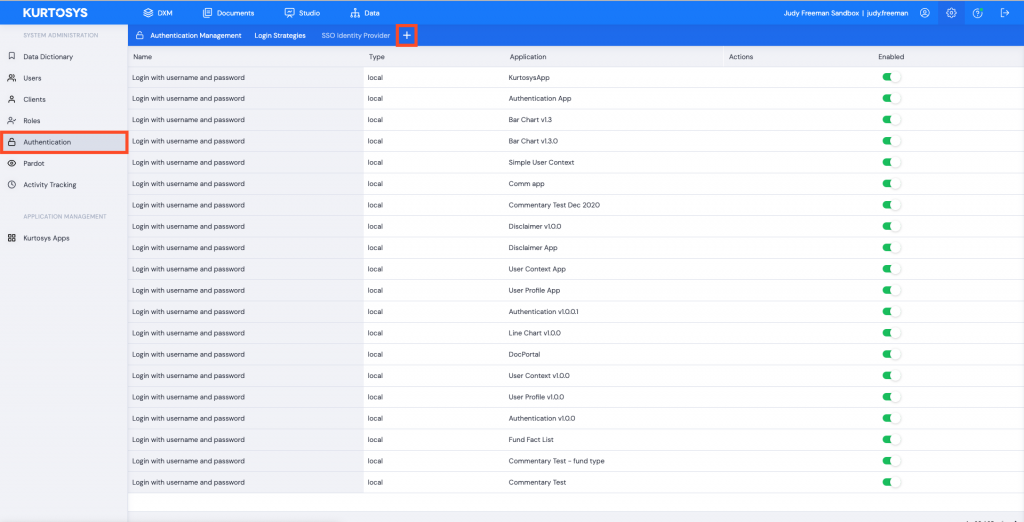
- Click + to add a new login strategy.
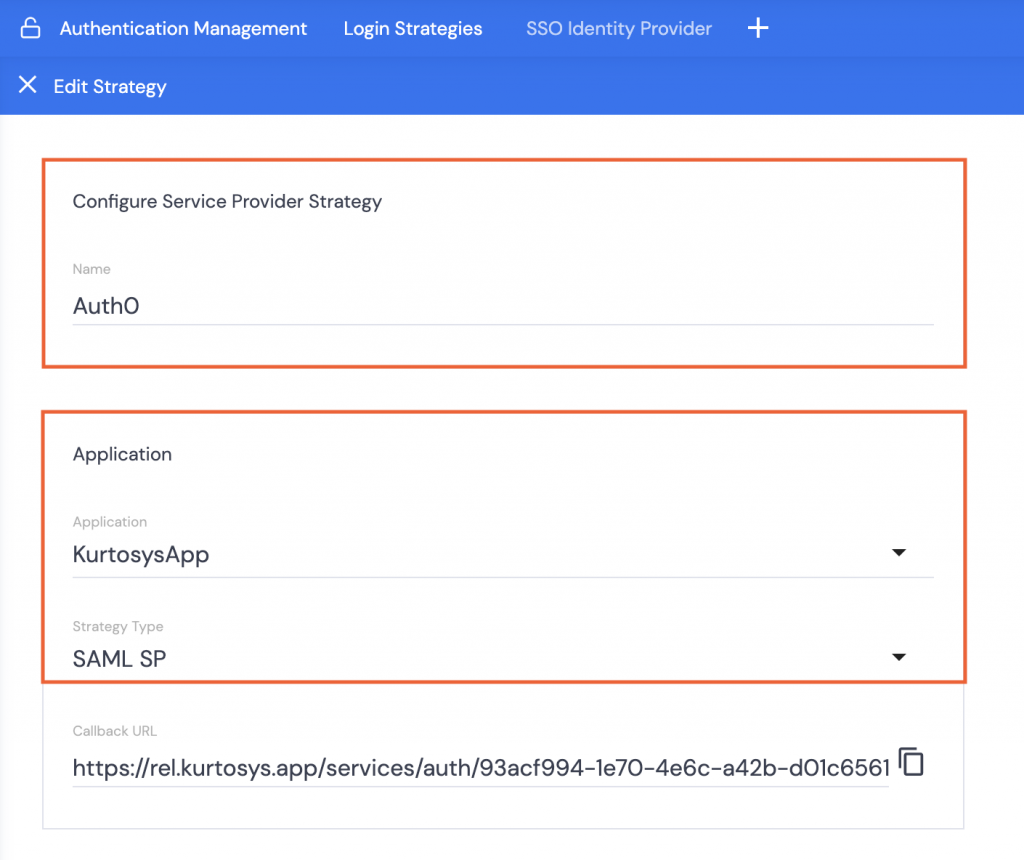
- Name the strategy, e.g. Auth0.
- Select which application is going to use this strategy e.g. KurtosysApp
- Select SAML SP as the Strategy Type. This will open the User Creation, Signing, Domain, and Authentication options.
User Creation
- Can be toggled off if the users already exist on the Kurtosys Client instance. Proceed to Signing.
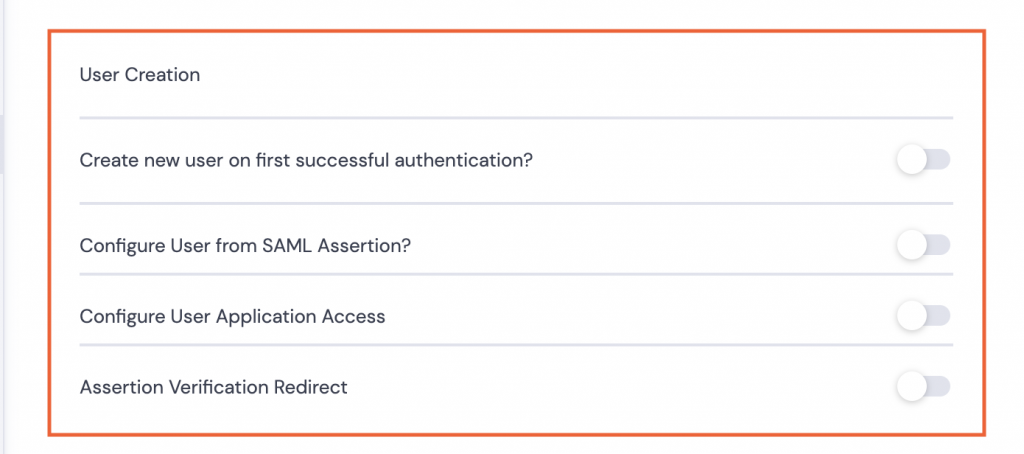
- If users need to be created or have user details updated, toggle on and complete the fields as necessary:
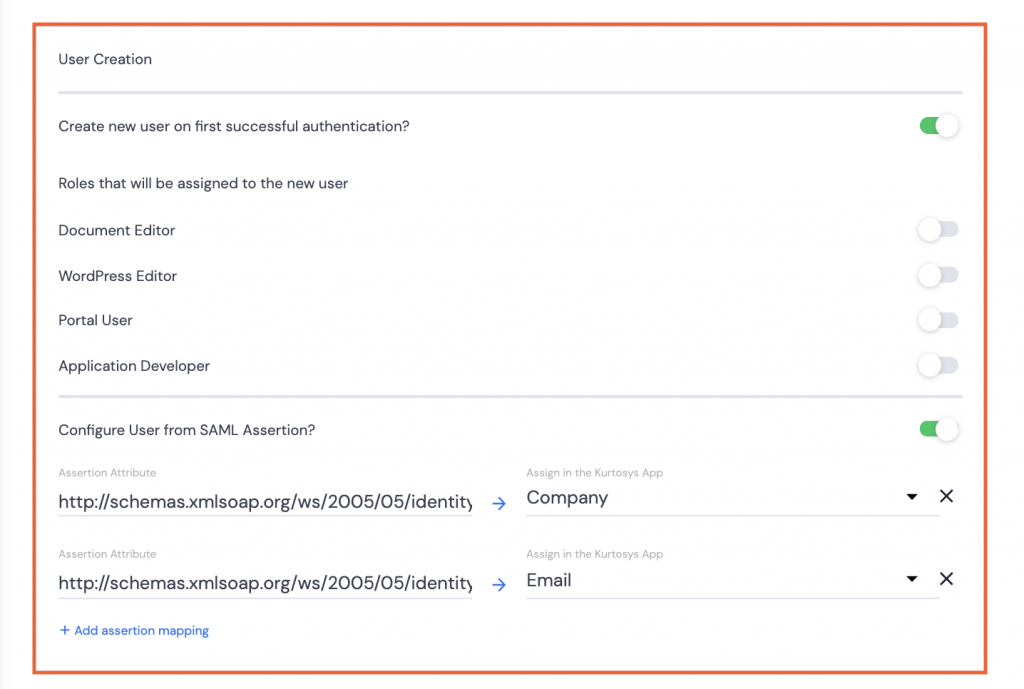
- Create new user… if the users do not already exist for the Kurtosys client instance.
Note: User roles can be assigned simultaneously with the user creation.
- Configure User from SAML Assertion? Use the SAML information like Email or Company to set up the user configuration to pull through to the User’s details in System Administration.
Note: Assertion mappings can be added as needed, but only a single email, a single Document Entitlement, and a single company name, although multiple roles can be assigned.
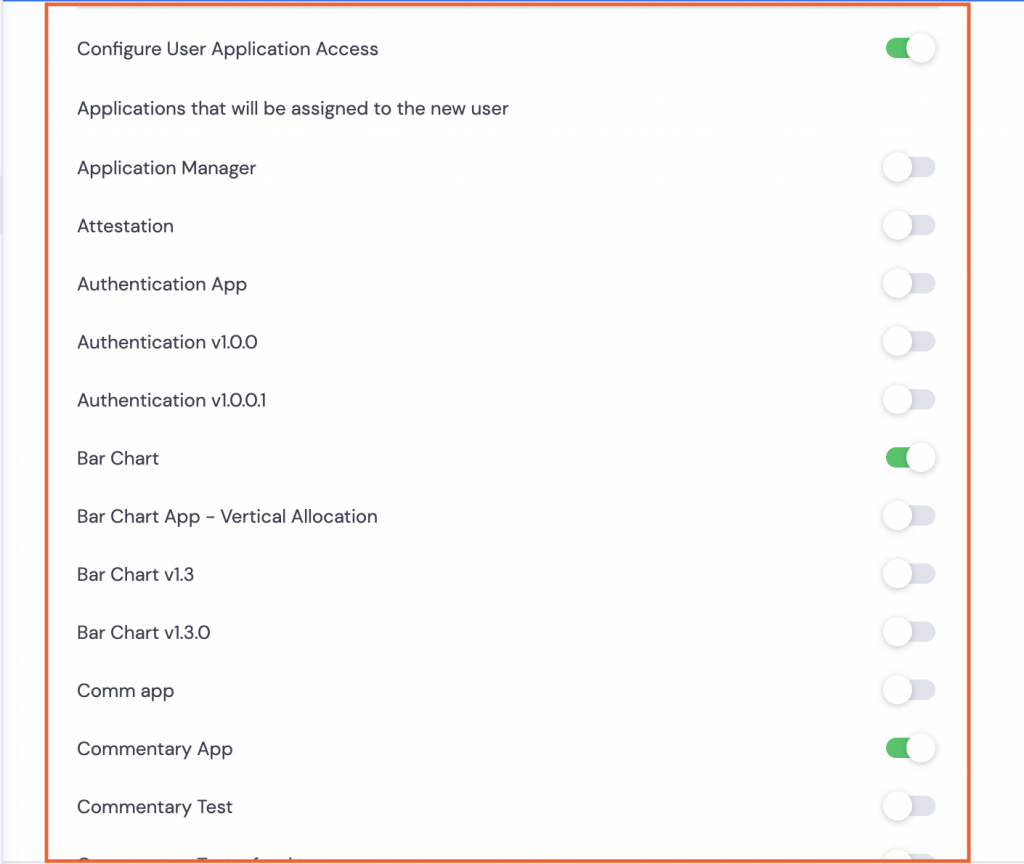
- Configure User Application Access Allocate access to specific applications only. Select from available applications.
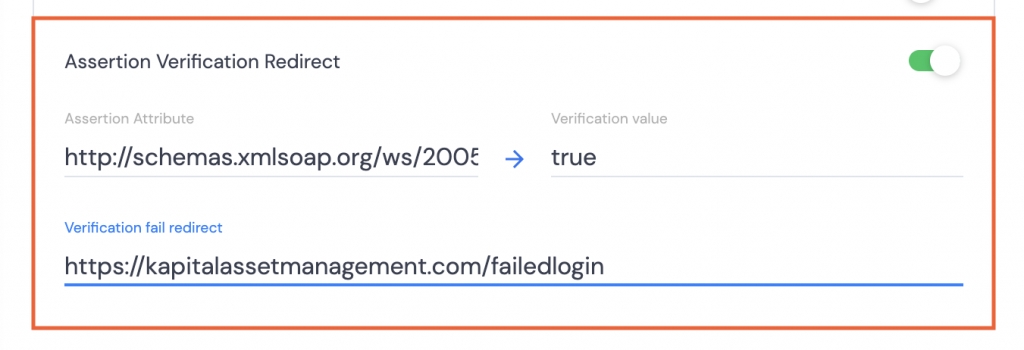
- Assertion Verification Redirect Ensure that users have been verified by checking a specific attribute. If the attribute does not match the requirement, redirect the user to a URL which supplies them with additional information as to how to fix the verification issue.
Signing
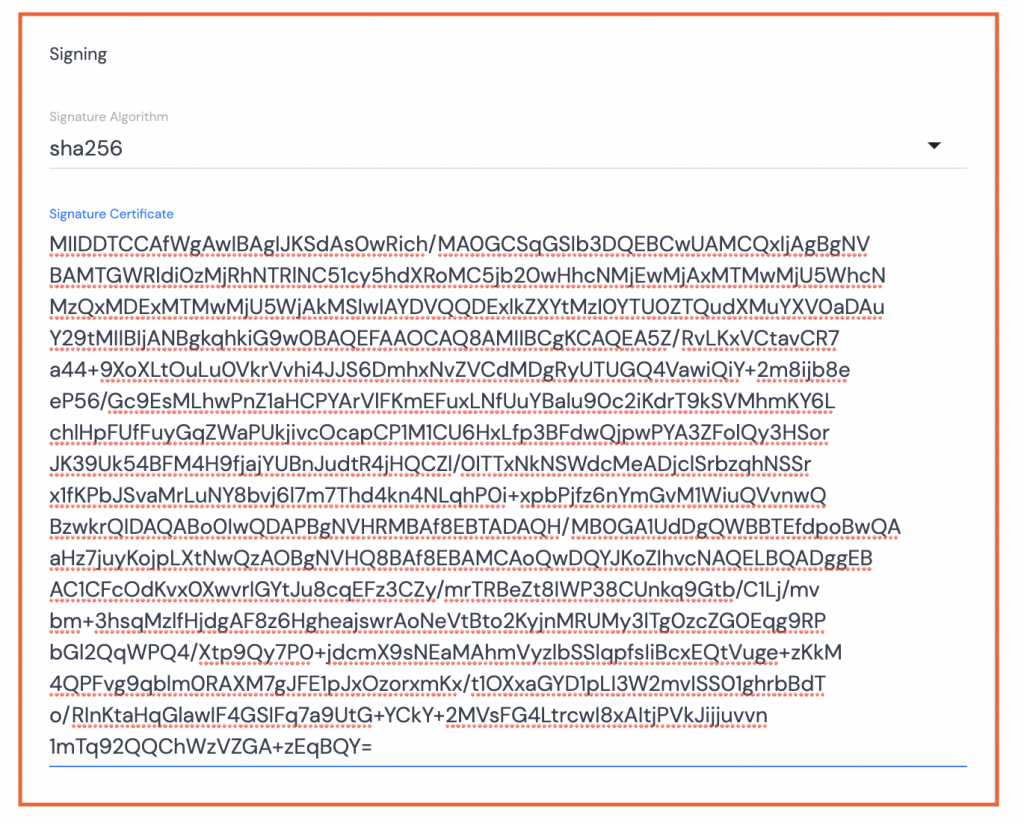
- Select sha256 for the Signature Algorithm.
- Open the downloaded Certificate using TextEdit or Notepad++ or similar.
- Copy the text between the BEGIN and END CERTIFICATE wording.
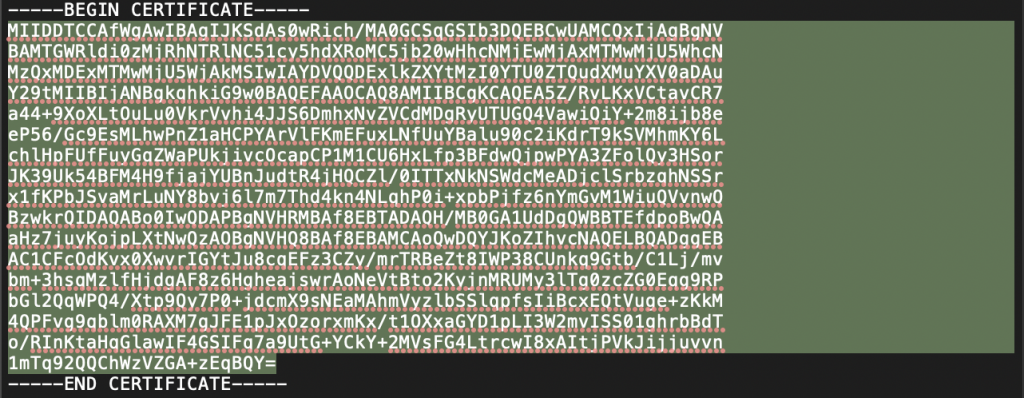
- Paste the text into the Signature Certificate field.
Domain
In Auth0:
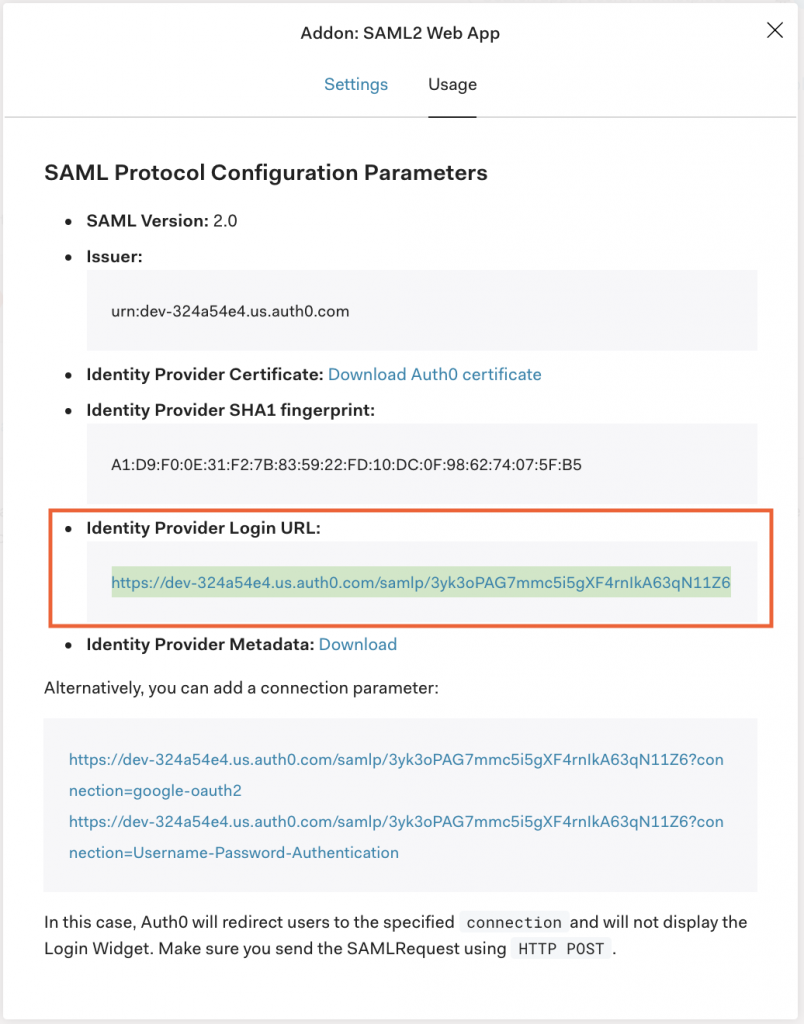
- Copy the Identity Provider Login URL.
In Kurtosys App:
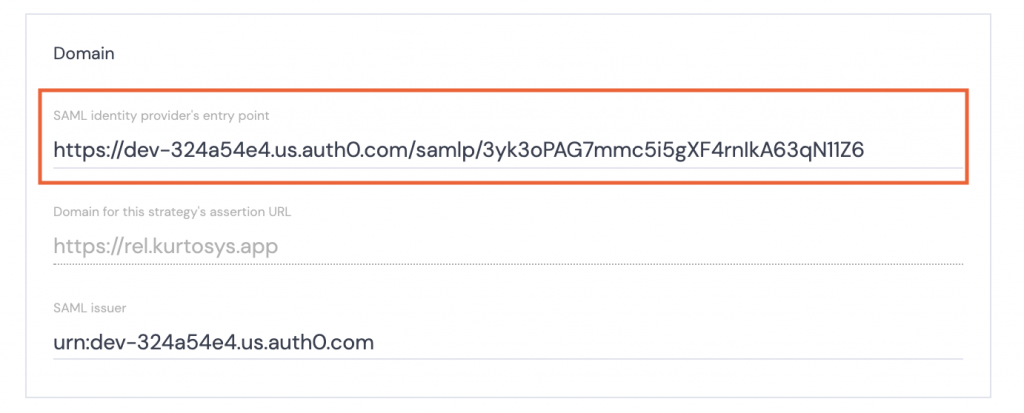
- Paste the Identity Provider Login URL in the SAML identity provider’s entry point field.
In Auth0:
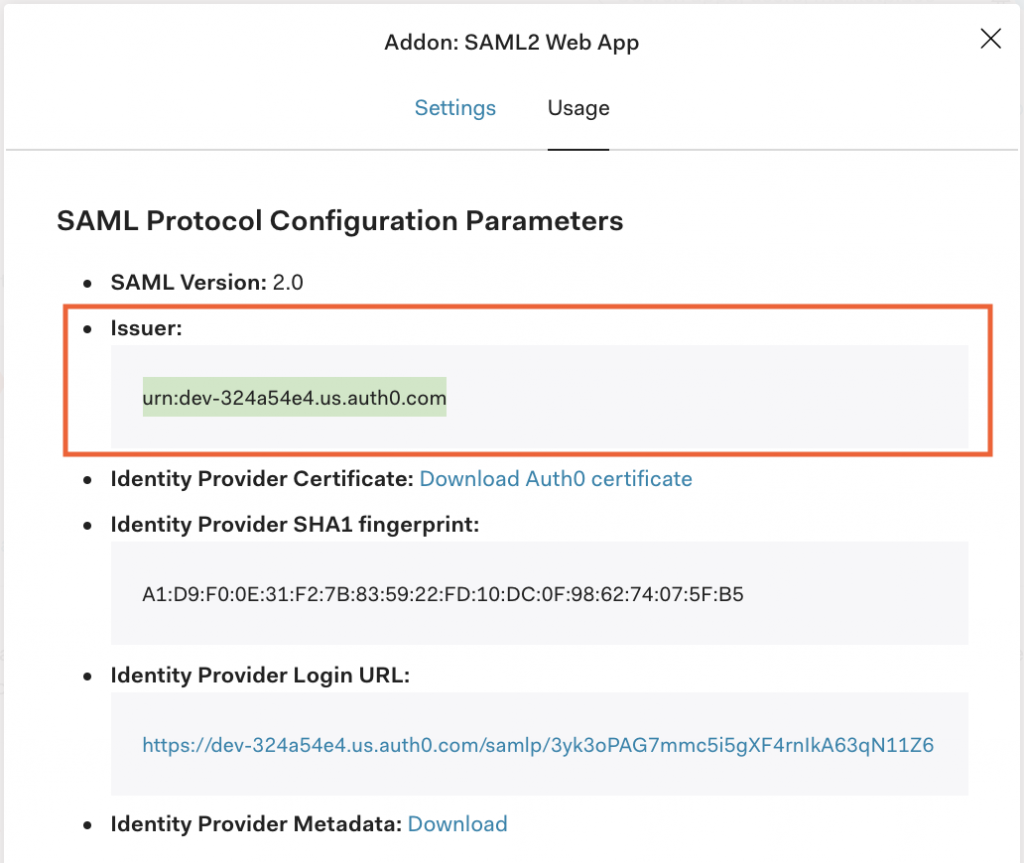
- Copy the Issuer urn.
In Kurtosys App:
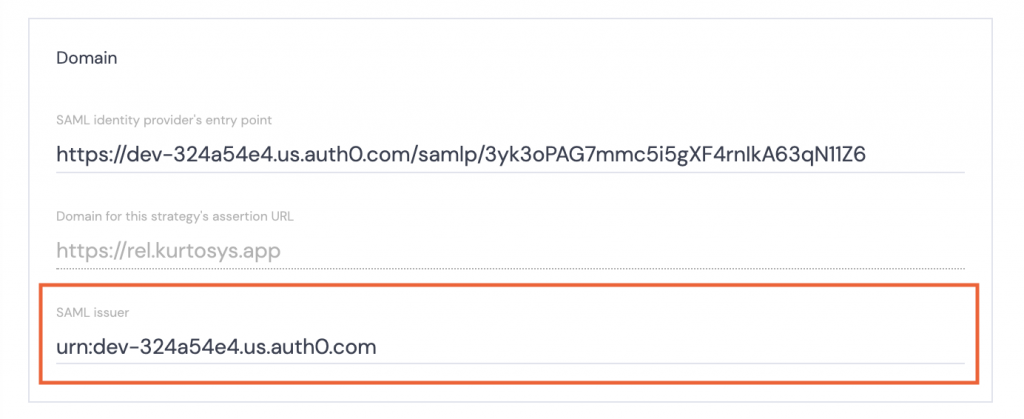
- Paste the Issuer urn into the SAML issuer field.
Authentication
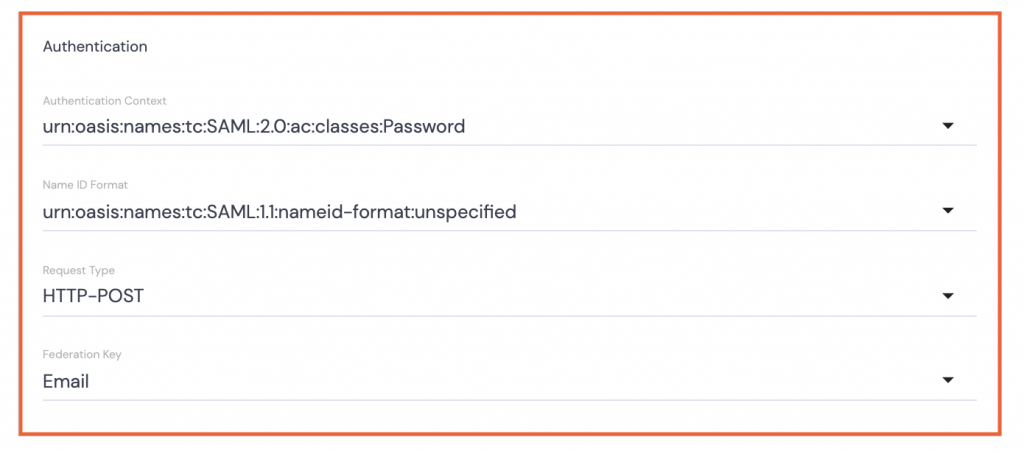
- Authentication Context: Select urn:oasis:names:tc:SAML:2.0:ac:classes:Password from the dropdown options.
- Name ID Format: Select urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified from the dropdown options.
- Request Type: Select HTTP-POST from the dropdown options.
- Federation Key: Select Email from the dropdown options.
- Click Save, then refresh the page.
- Click the Auth0 strategy name to reopen it.
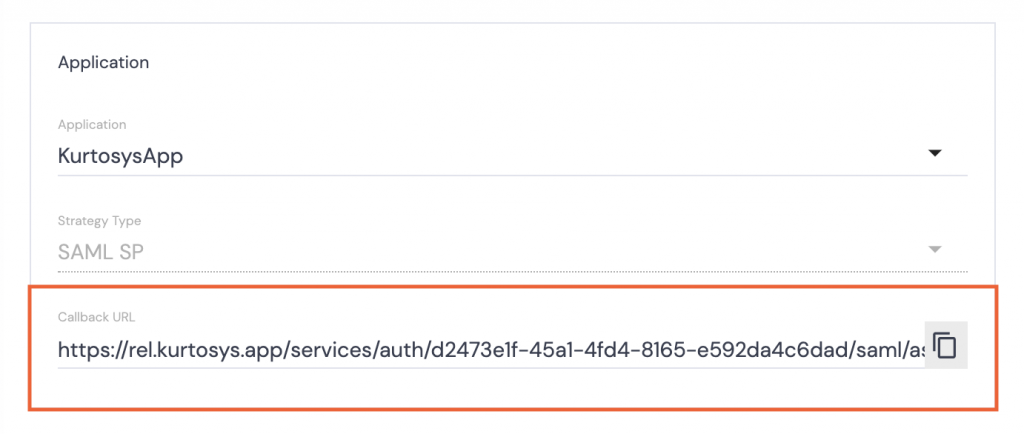
- Click the copy button next to the Callback URL.
- Click Save.
![]()
- Toggle on the Auth0 strategy.
In Auth0:
Under the Settings tab.
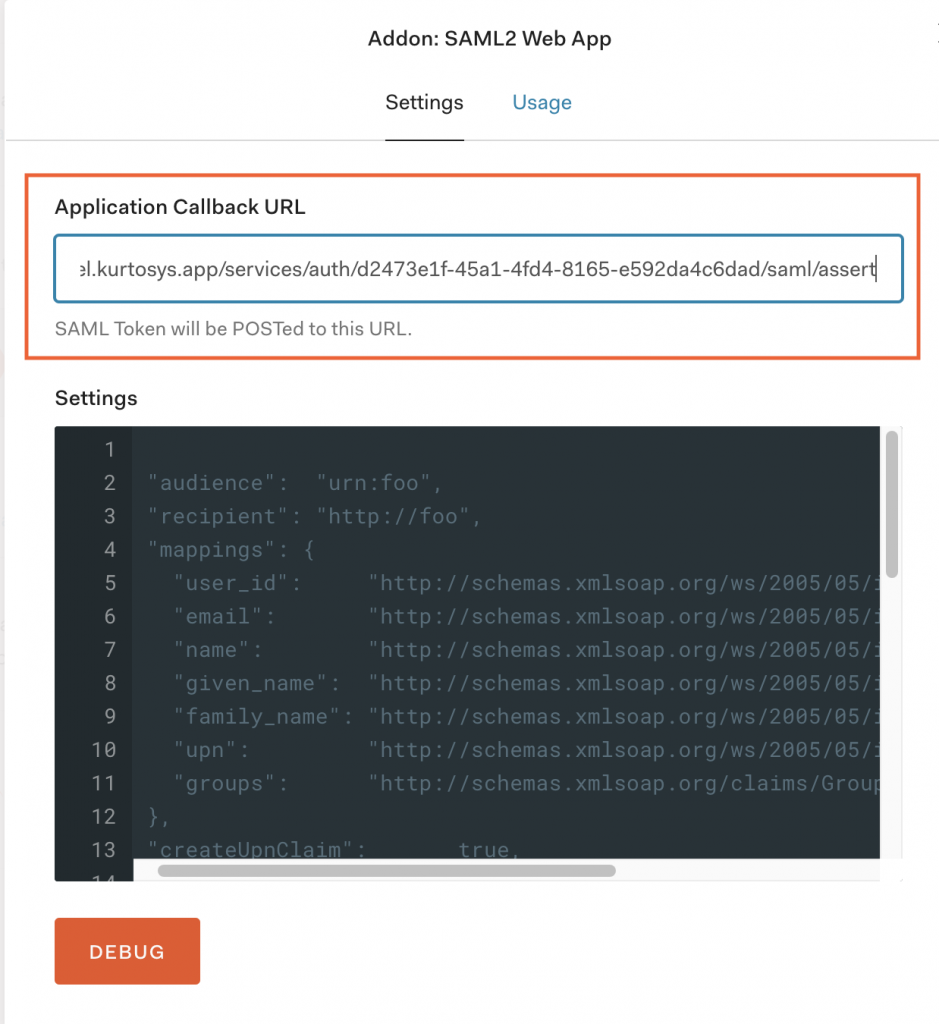
- Paste the Callback URL into the Application Callback URL field.
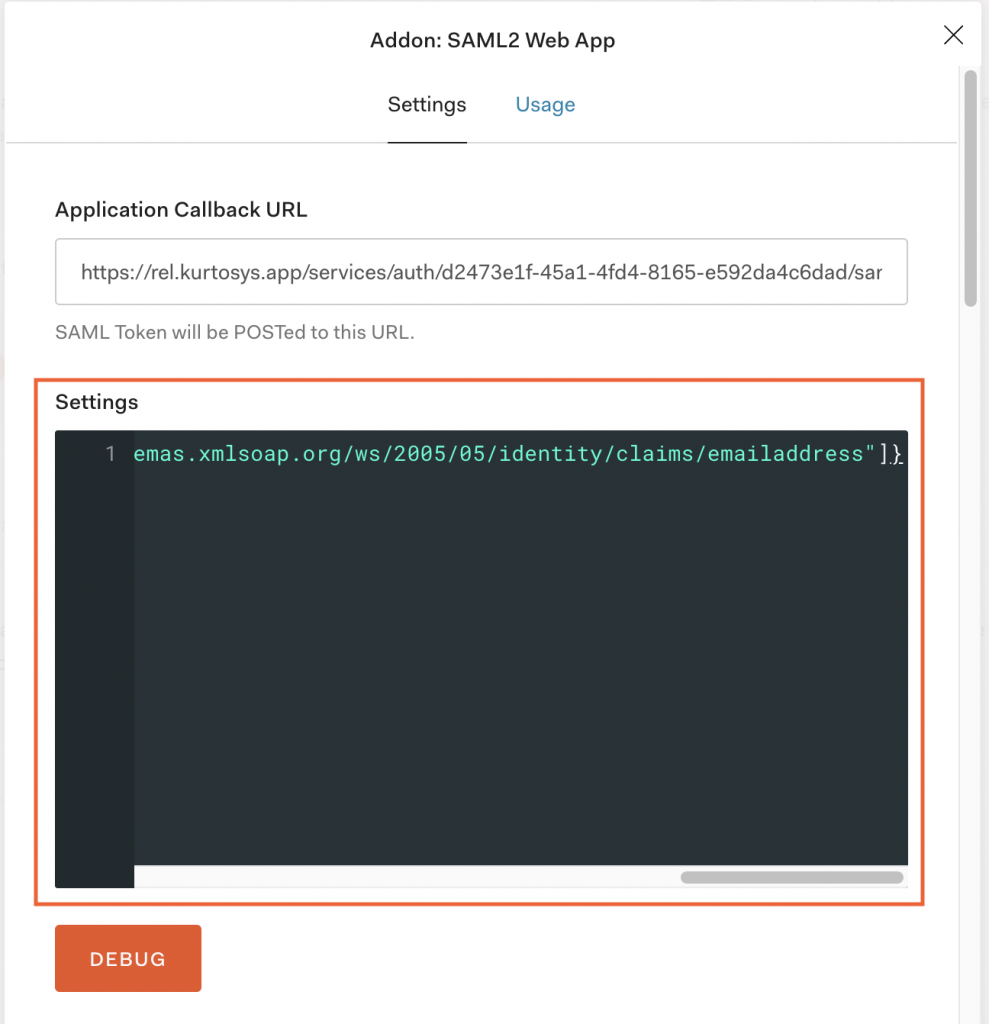
- Delete the JSON in the Settings field.
- Use the applicable
nameidentifierJSON mappings into the Settings field.
- Scroll down and click the ENABLE button.
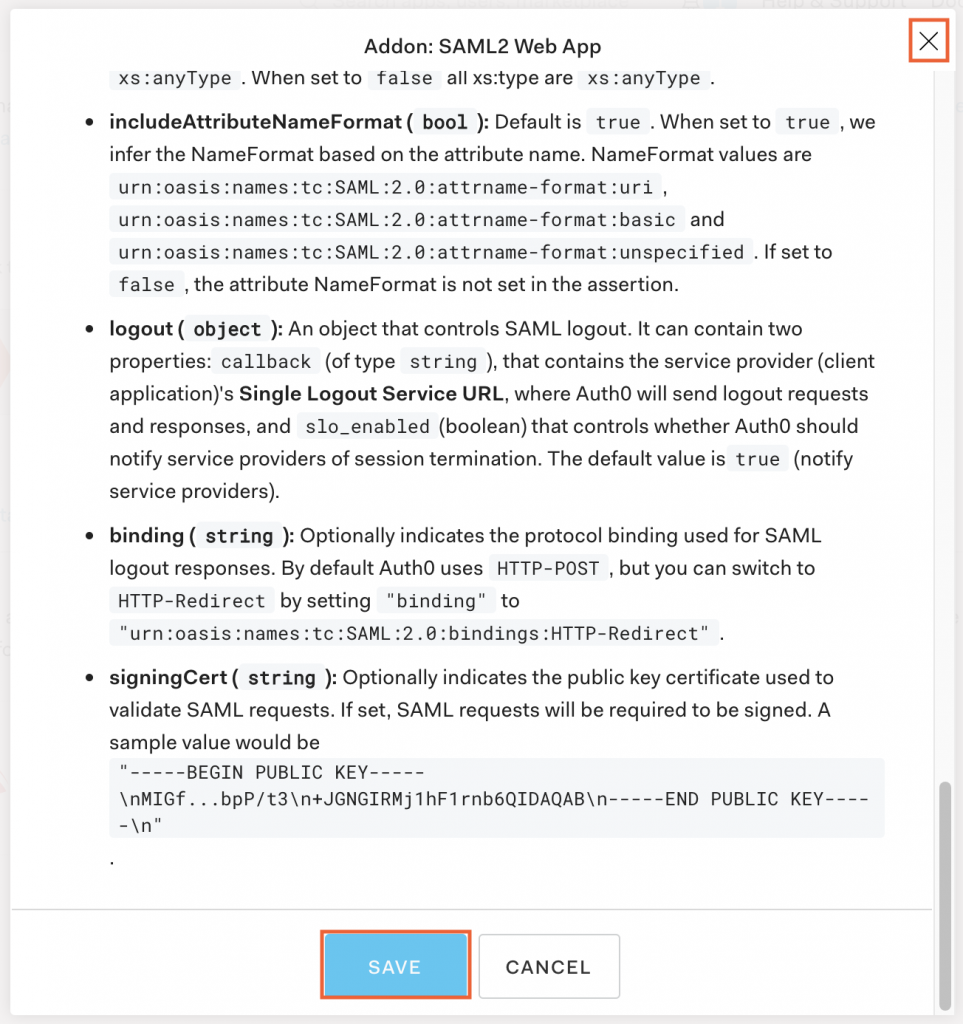
- Click SAVE then X to close.
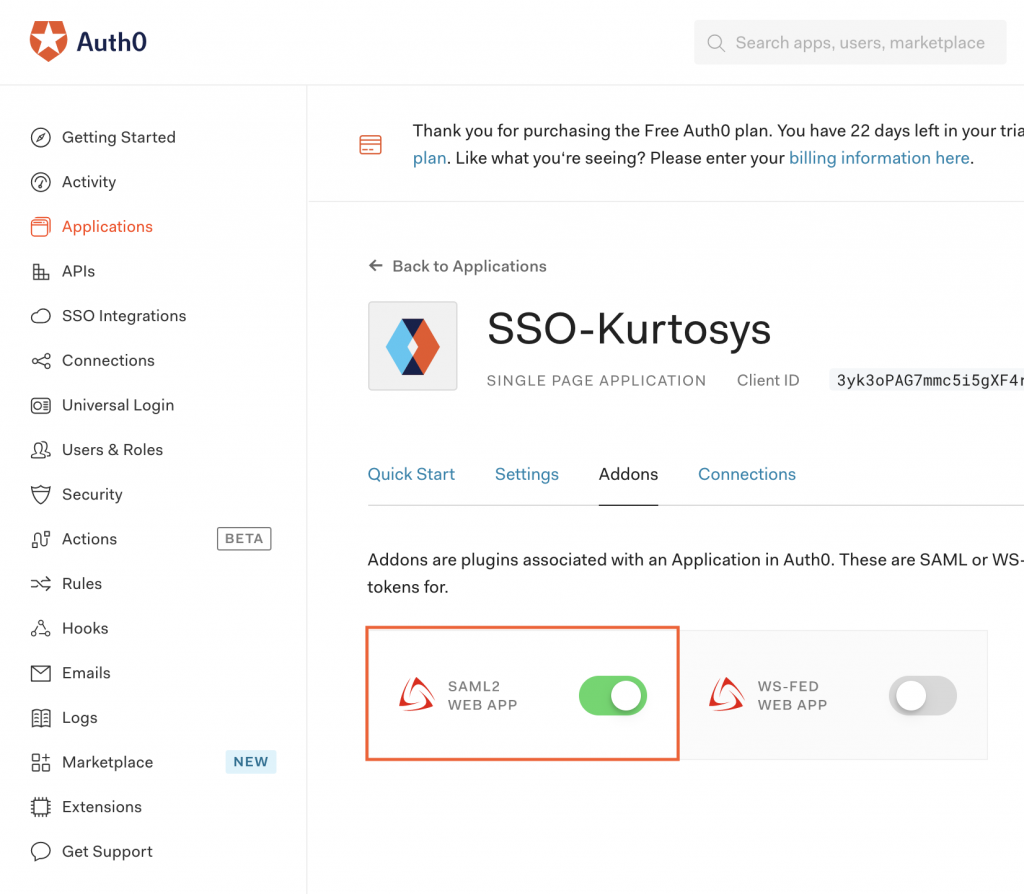
The SAML2 WEB APP is now enabled and active.
Auth0 Users
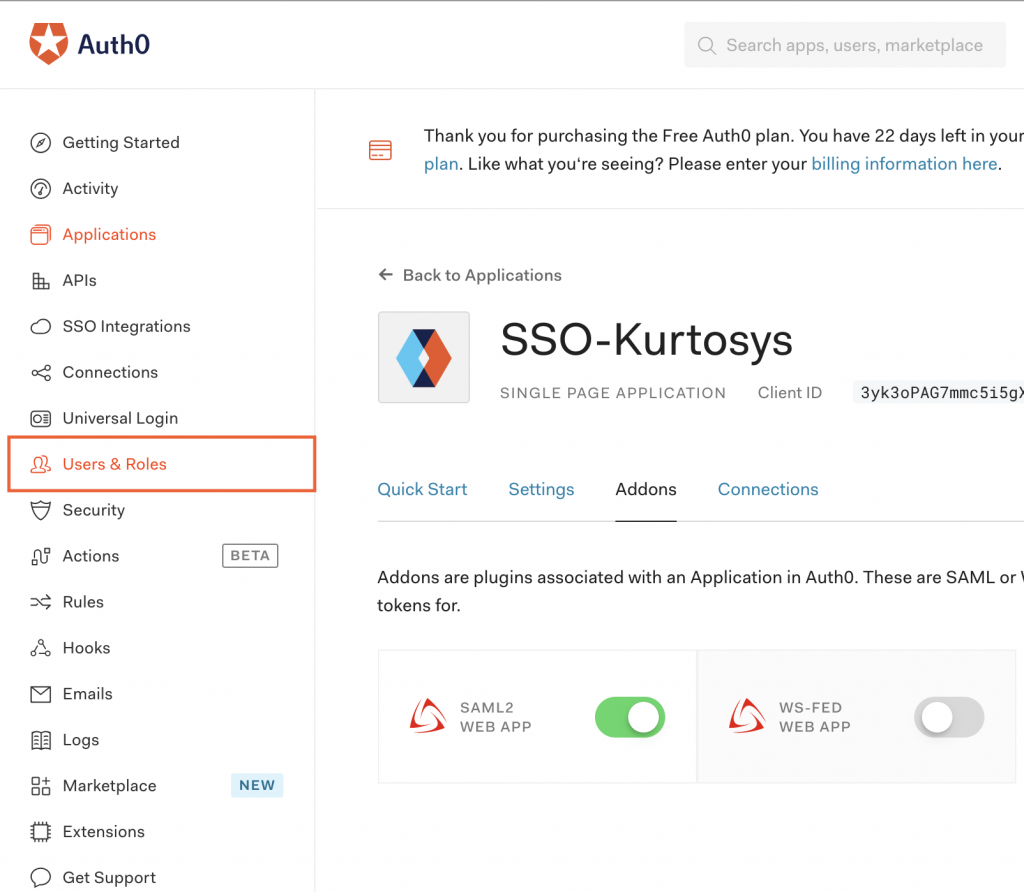
- Click the Users & Roles tab.
- Click Users.
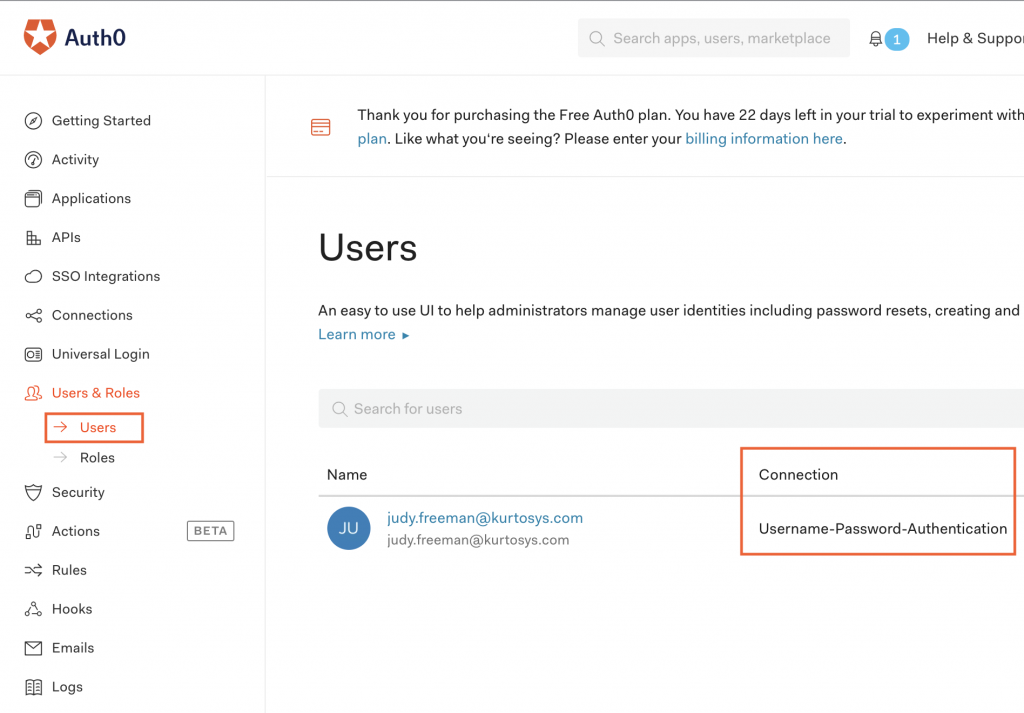
- Ensure that all users are listed with Username-Password-Authentication as their Connection selection.
Testing

- Log in to your Kurtosys Client Instance by selecting the SAML SP option.
Note: You can disable the "local" login strategy to force user to login using Auth0 only.
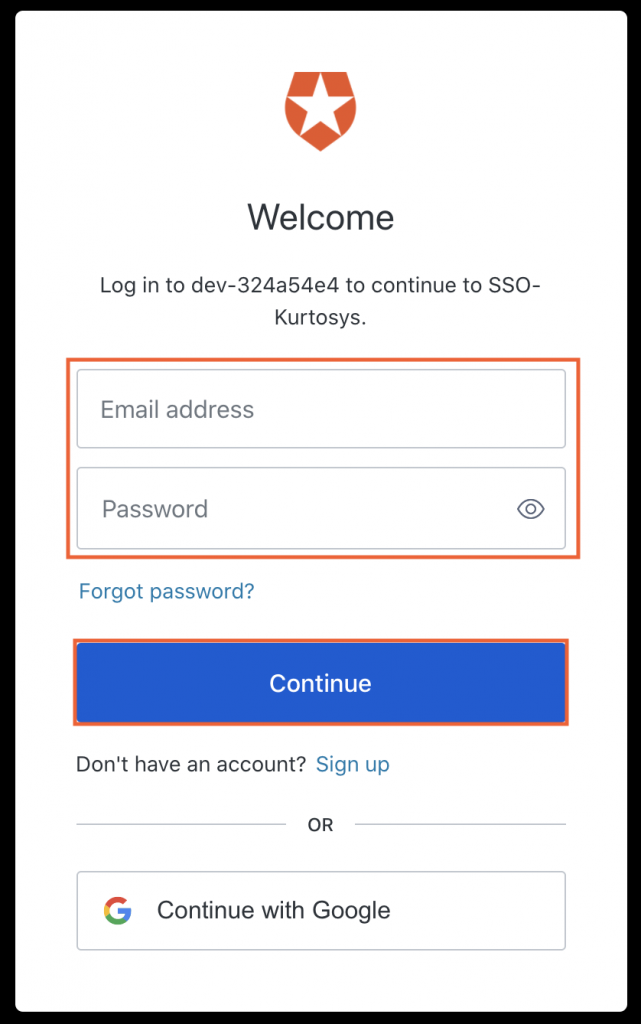
- In the Auth0 pop-up, enter the Email address and Password for the Auth0 user.
- Click Continue.
If everything is set up correctly, you will be logged in to the Kurtosys client instance.
