Users
Users are the individuals who will be logging into either the Kurtosys App or the Document Portal to access applications, information or documentation. Each action a user makes is logged as part of the User Activity Tracking.
User Impersonation
User Impersonation allows a User to log activity as another User – by using their Username. This is typically used when assisting another user with a task they are unfamiliar with or if a Client Admin user needs to see what the other user is experiencing regarding entitlements or other restrictions.
Use the Settings cog to access the System Administration tools.
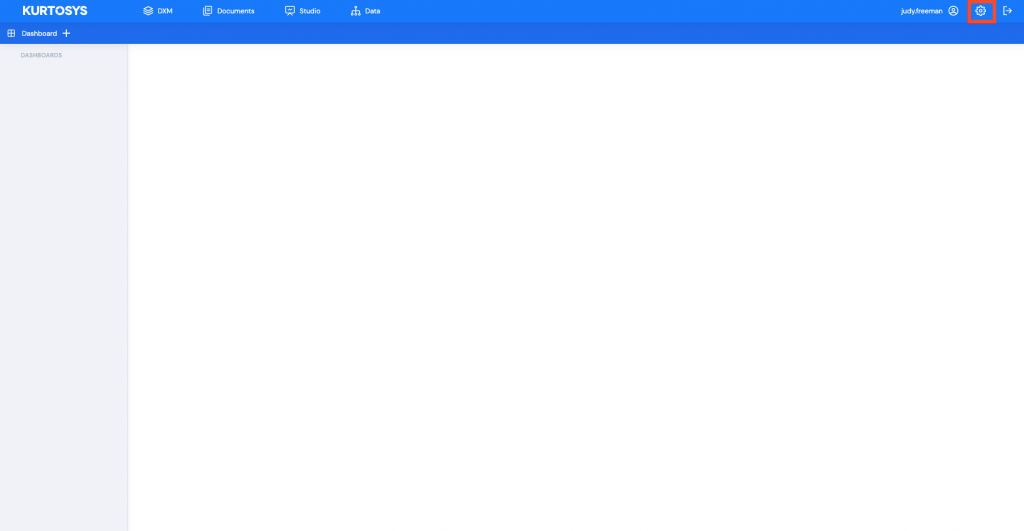
- Click Users in the navigation pane to access all existing Users. This will open the Users information screen. Any existing Users will be listed in the table along with their login details.
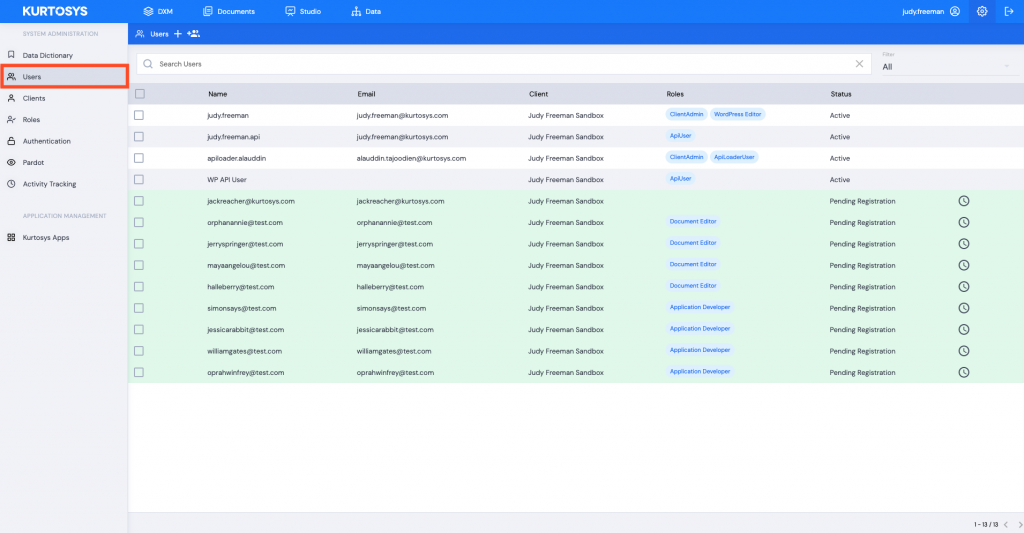
- Click the Username you are going to allow to impersonate other Users.
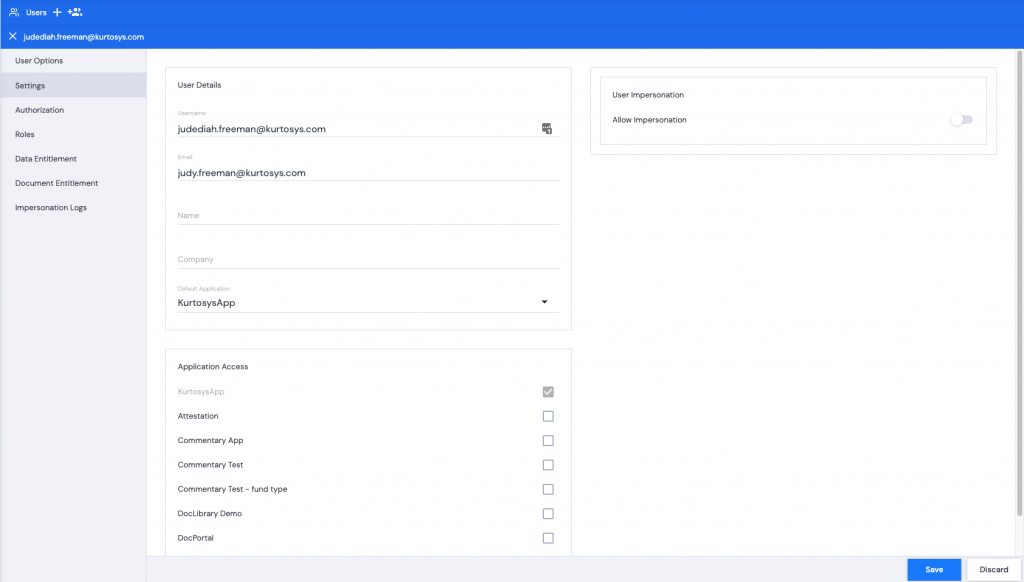
- Toggle Allow Impersonation on.
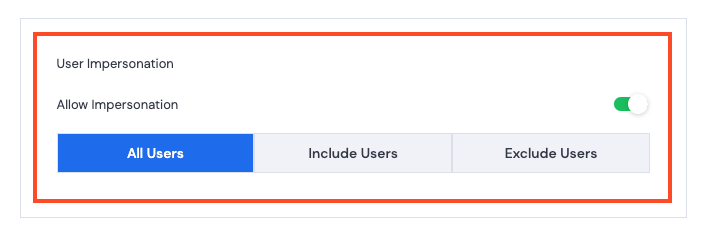
- Select one of the following:
- All Users – allow this User to impersonate any other User.
- Include Users – allow this User to impersonate selected users. Click a user’s name to add them to the Included Users list.
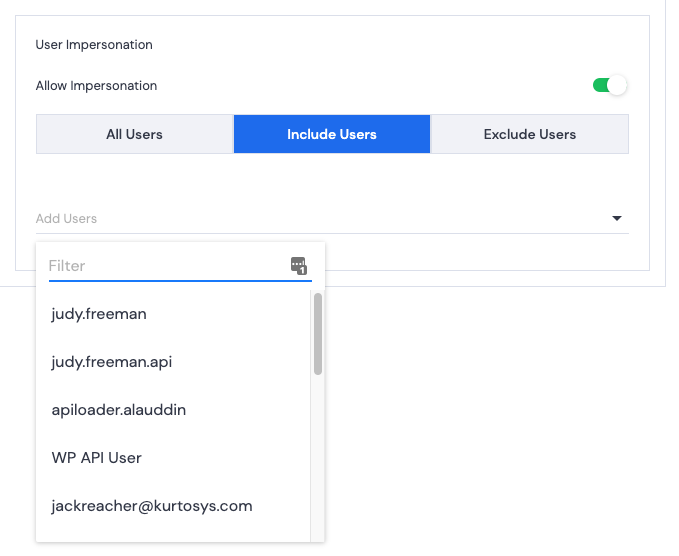
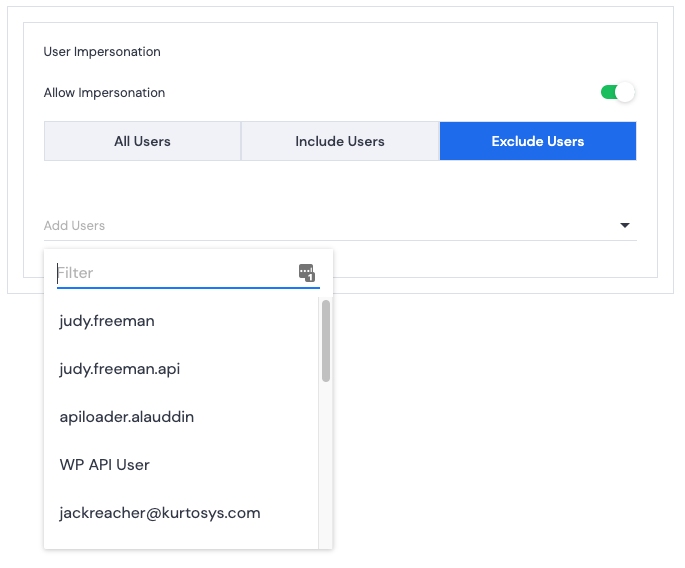
- Exclude Users – restrict this User from impersonating selected users. Click a user’s name to add them to the Excluded Users list.
- Click Save. A green successful task pop up bar will display across the bottom of the screen.
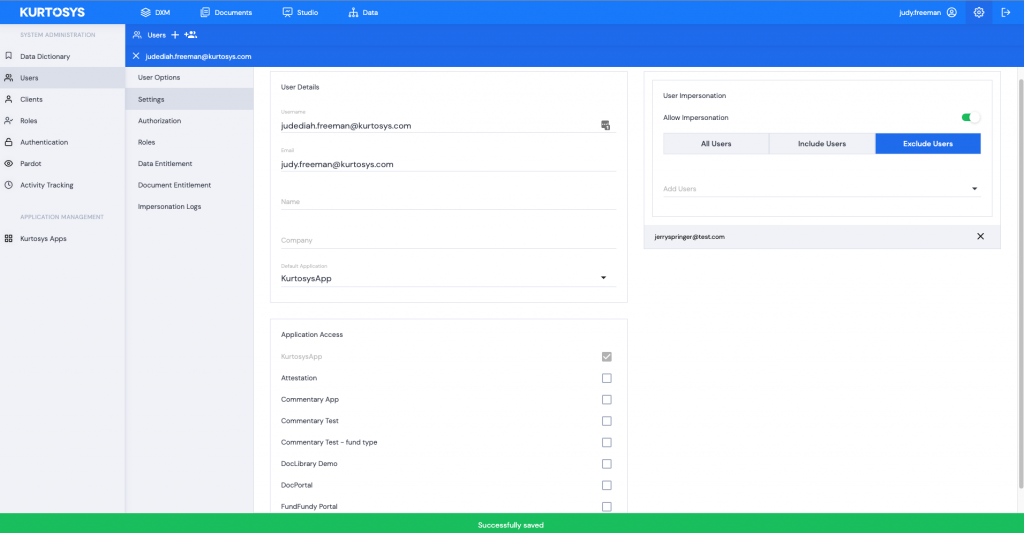
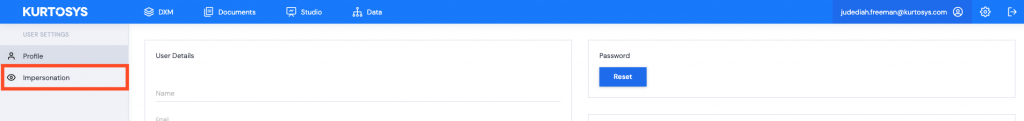
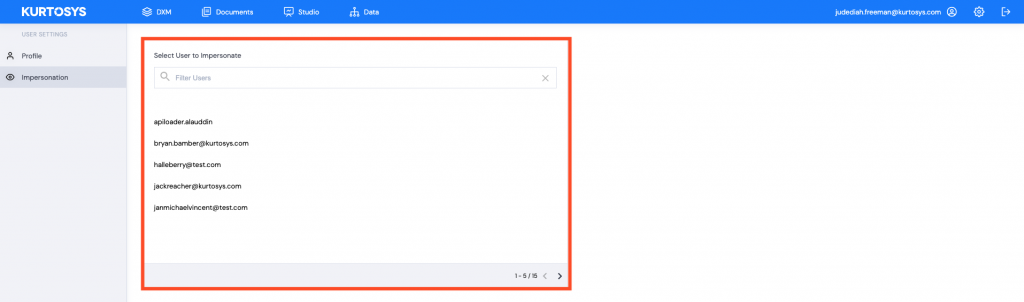
- The User who has been given impersonation rights can now click on their profile.

- Click Impersonation.
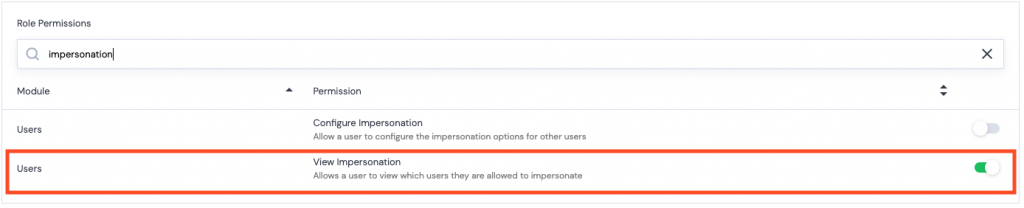
Note: the user being given Impersonation rights will need to have the following permission set for their Role.
Users > Roles
The list of users displayed will be per the impersonation permissions you were given in step 4. (All, Include, or Exclude)
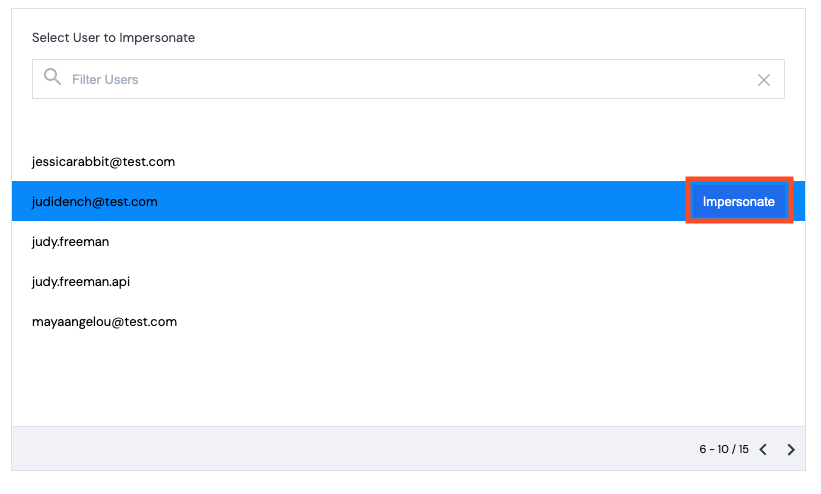
- Hover over a username to access the Impersonate button.
Impersonation becomes active.
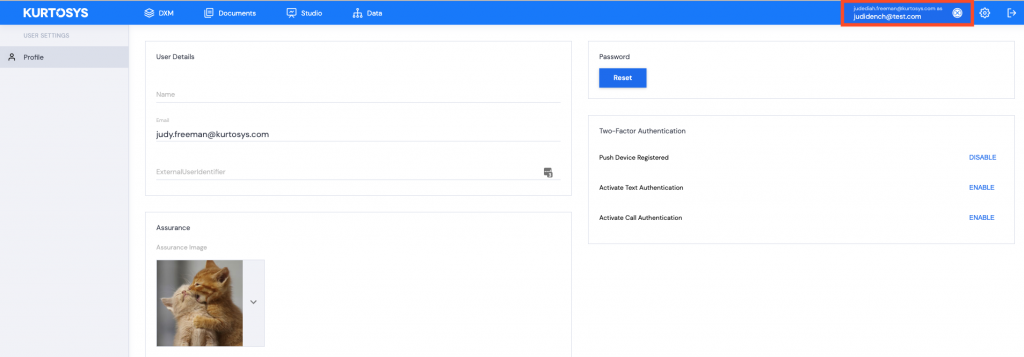
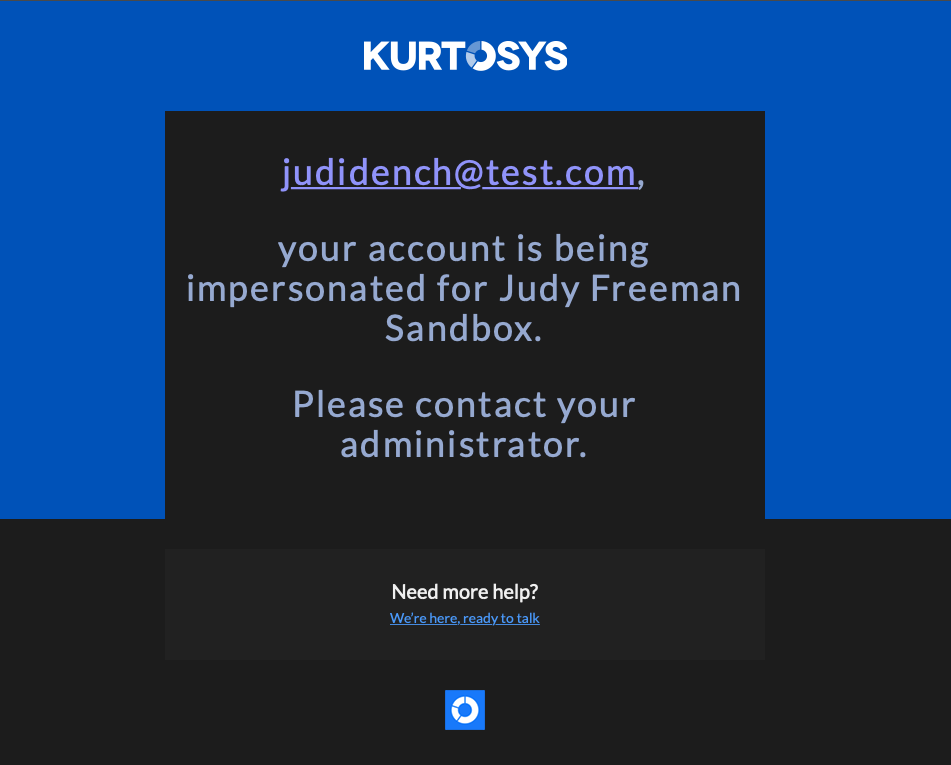
The user being impersonated will receive an email notifying them that their username is being impersonated on a specific client instance. If this is being done without permission, the user can contact an administrator.
End Impersonation
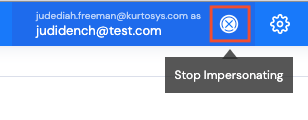
Click the ⊗ next to the impersonation name to Stop Impersonating.
See also Adding Bulk Users, Adding a Role and Locking & Deactivating a User.
