Single Sign-on (SSO) permits a user to use a set of login credentials set up in one Identity Provider (IdP) application to access Service Provider applications which significantly simplifies the login process. This feature is extremely useful for enterprise-level companies that use multiple software platforms on a daily basis and need better user-account management.
Kurtosys is an SSO provider which means users can log into the Kurtosys platform and Kurtosys portals using their credentials from other applications that use the common SAML 2.0 authentication protocol. This eliminates the need for users to set up and remember multiple passwords, thus reducing password fatigue and improving security.
Table of Contents
Setting up Single Sign-On
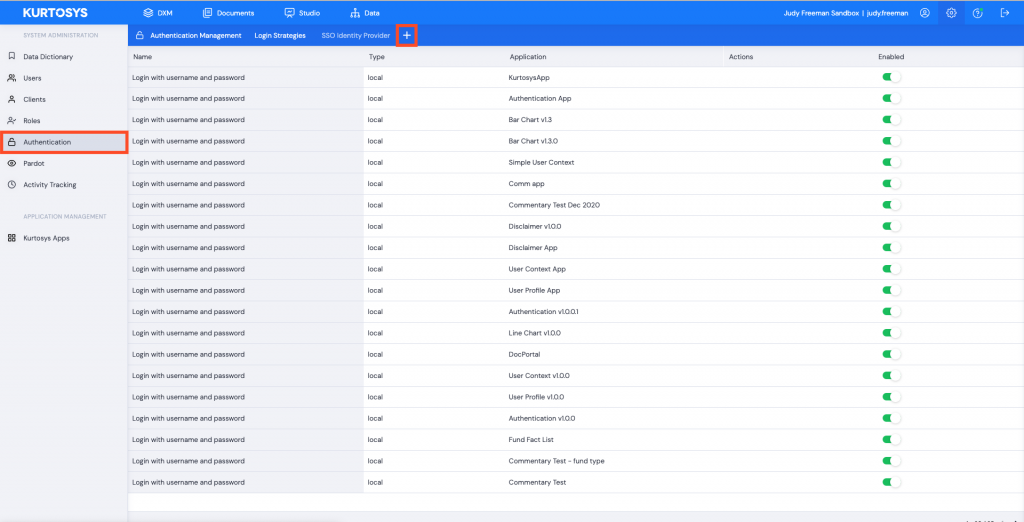
Use the Settings cog to access the System Administration tools.

- Click the Authentication tab.
- Click + to add a new Login Strategy.
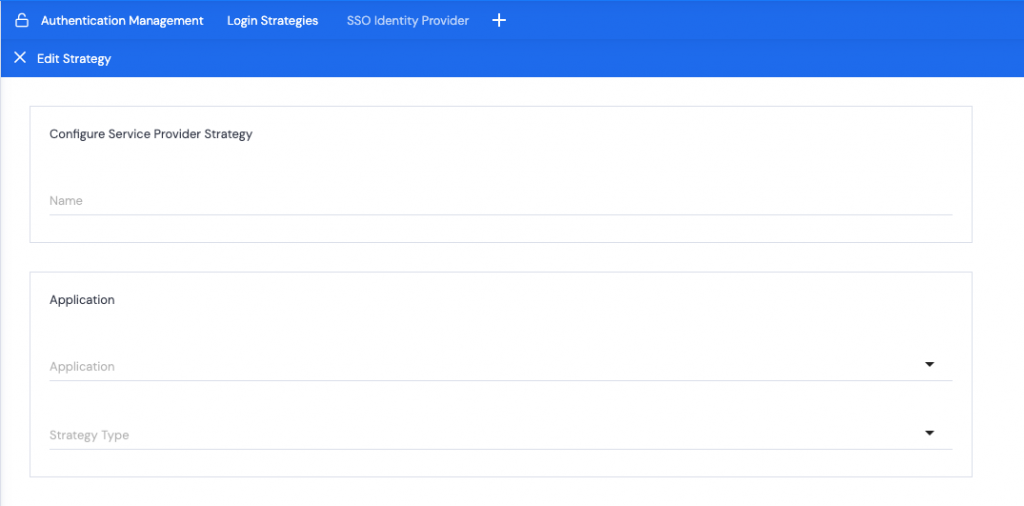
- Name your Strategy. It is best to name it per the application you are using for SSO. This way, if you add additional strategies, they’re easily identifiable if you need to make amendments or edits.
- From the dropdown, select which Application this strategy will be used for, e.g. Kurtosys App or a Document Portal.
- Select the Strategy Type (which application to use as your identity provider) from the dropdown list.
- SAML SP – this will use the other application’s login information to log in to the Kurtosys App or Document Portal.
- SAML IDP – this will use Kurtosys App login information for the SSO.
SAML SP
Using another application as the identity provider.
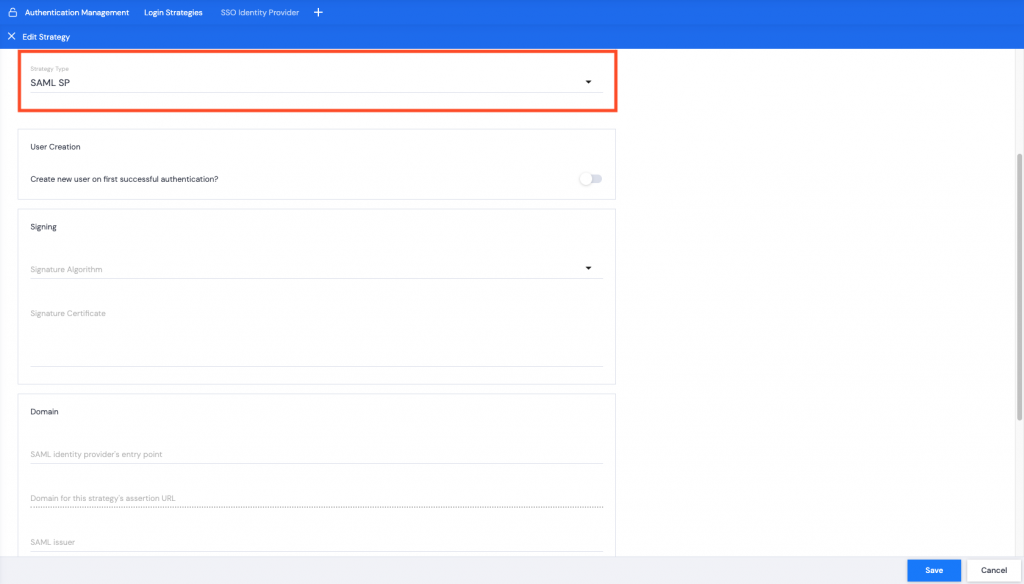
User Creation
If users have already been added to the Kurtosys Client Instance:
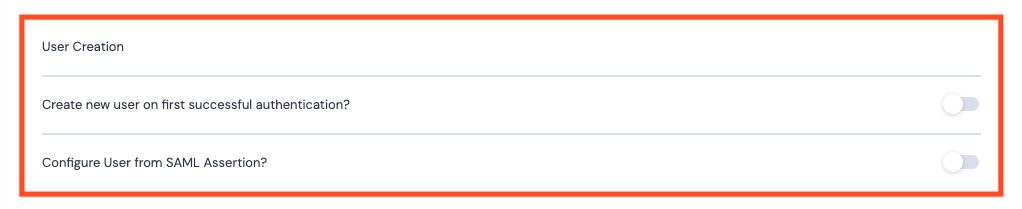
- Can be toggled off. Proceed to Signing.
If users do not yet exist:

- Create new user on first successful authentication? – Toggle on. This selection will automatically create a new User in the Kurtosys App when the other application’s login information is first used to log in.
- Roles that will be assigned to the new user – If User Creation is toggled On, you can select from the list of existing roles to assign to the new users by toggling the role options On.
Configure User from SAML Assertion?
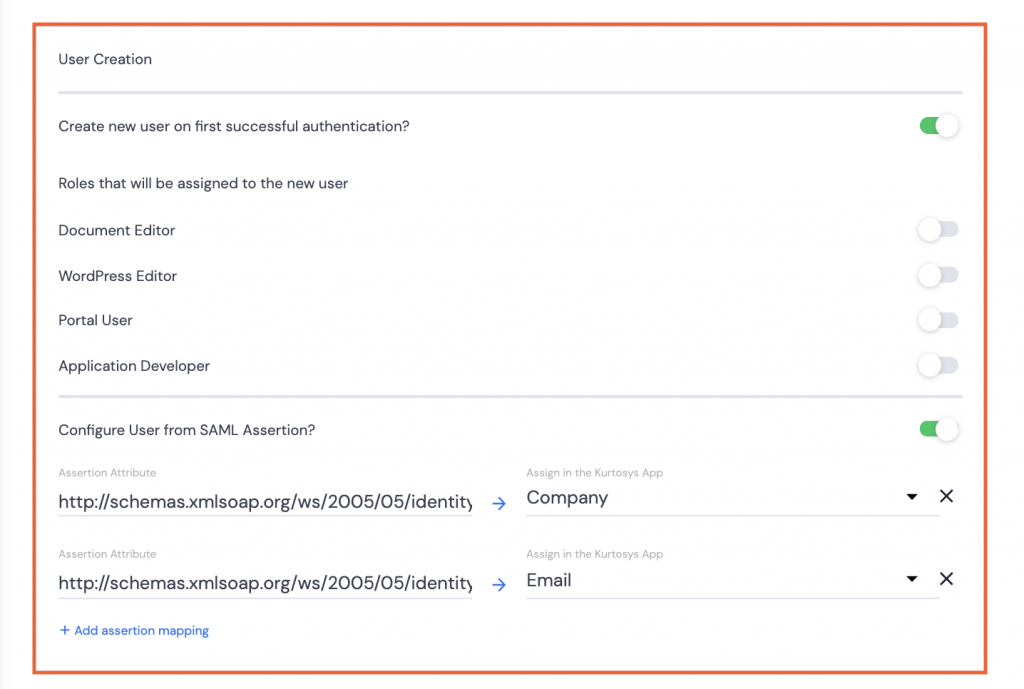
- If users need to be created or have user details updated, toggle on, and complete the fields as necessary:
- Create new user… if the users do not already exist for the Kurtosys client instance.
Note: User roles can be assigned simultaneously with the user creation.
- Configure User from SAML Assertion? Use the SAML information like Email or Company to set up the user configuration to pull through to the User’s details in System Administration.
Note 1: Assertion mappings can be added as needed; a single email, a single company name and a single Document Entitlement Preset, but multiple roles can be assigned.
Note 2: If roles have been set with the option under Create new user on first successful login, these roles will be amended if there are Assertion mappings used.
Signing
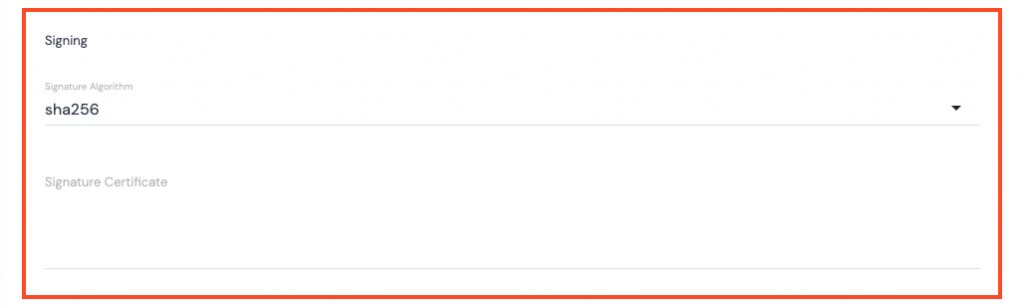
- Signature Algorithm – use the dropdown list to make your selection, sha256 (Secure Hash Algorithm 2) is the only one currently available.
- Signature Certificate – this can be obtained from the identity provider. The Signature Certificate authenticates identity and service providers.
Domain
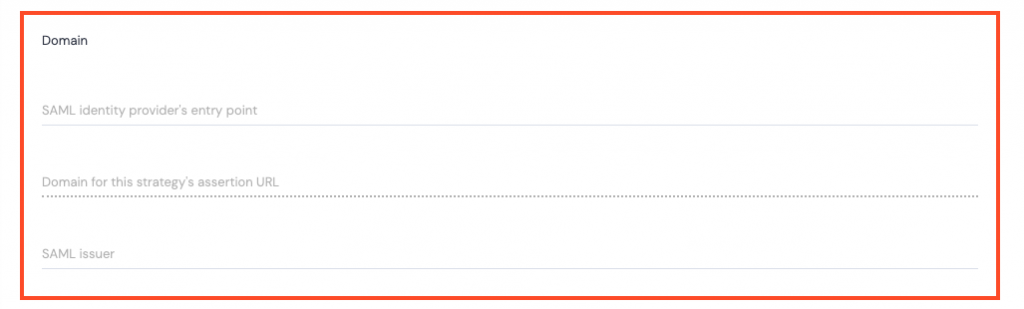
- SAML identity provider’s entry point – the URL to where the User is redirected to confirm their identity; this is obtained from the identity provider.
- Domain for this strategy’s assertion URL – the Kurtosys App URL.
- SAML Issuer – this is the unique identifier for the identity provider (other application for login information).
Authentication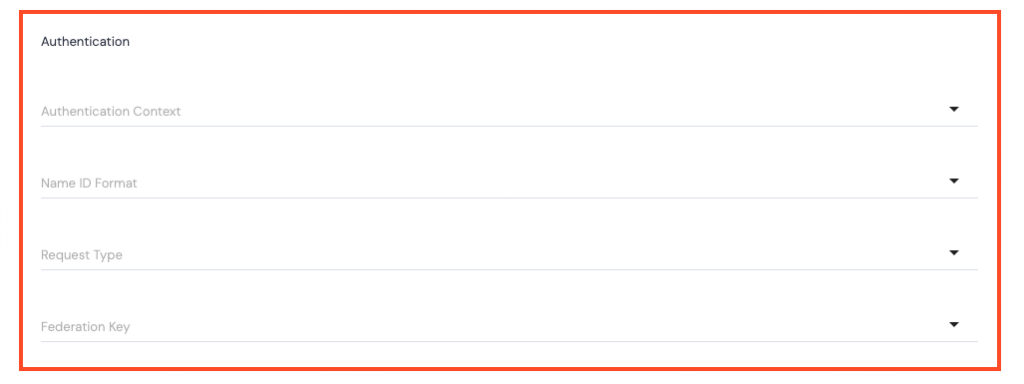
- Authentication Context – use the dropdown arrow to select one of the following:
- urn:oasis:names:tc:SAML:2.0:ac:classes:Password – Password is presented to the app over an unprotected HTTPS session.
- urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport – Password is presented to the app over a protected session.
- urn:oasis:names:tc:SAML:2.0:ac:classes:TLSClient – A client certificate, secured with the SSL/TLS transport, is presented to the app for authentication.
- urn:oasis:names:tc:SAML:2.0:ac:classes:X509 – A digital signature, where the key was validated as part of an X.509 Public Key Infrastructure, is presented to the app for authentication.
- urn:federation:authentication:windows – The user’s Windows credentials are presented to the app for authentication.
- http:/ /schemas.microsoft.com/ws/2008/06/identity/authenticationmethod/windows – The user’s Windows
domain\usercredentials are presented to the app for authentication. - urn:oasis:names:tc:SAML:2.0:ac:classes:Kerberos – A password to a local authentication authority is used to obtain a Kerberos ticket, which is then presented to the app for authentication.
- Name ID Format – use the dropdown arrow to specify the Name ID Format that should come from the Identity Provider:
- urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress – the app expects the Name ID in an email address format.
- urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified – the format is specified at the identity provider level and the app parses the incoming Name ID Format.
- urn:oasis:names:tc:SAML:2.0:nameid-format:persistent – a persistent identifier is used for authentication to the app.
- urn:oasis:names:tc:SAML:2.0:nameid-format:transient – a random string of characters, that isn’t fixed for a user, is used for authentication to the app.
- Request Type – use the dropdown arrow to select from the following options:
- HTTP-Redirect – the data is redirected from the identity provider to the app.
- HTTP-POST – the data is posted from the identity provider to the app.
- Federation Key – use the dropdown arrow to select from the following options:
- Email – the user’s email address will be used to authenticate their login.
- ExternalUserIdentifier – the External User Identifier that can be viewed in a user’s User Profile section of the Kurtosys app is used to authenticate their login.
- UserName – the user’s Kurtosys app username is used to authenticate login.
Click Save. A green successful task pop up bar will display across the bottom of the screen.
SAML IDP
Kurtosys is selected as the Identity Provider.
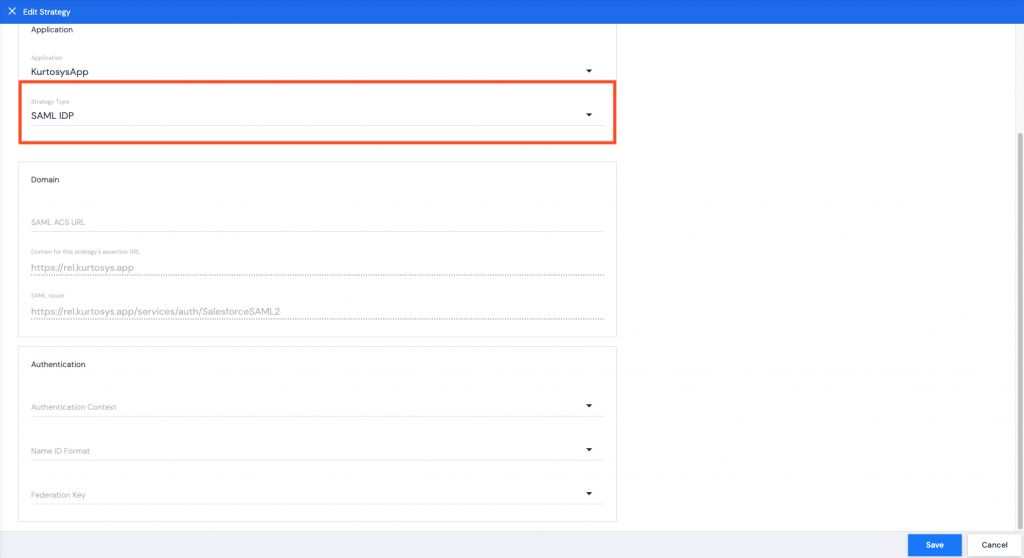
Domain
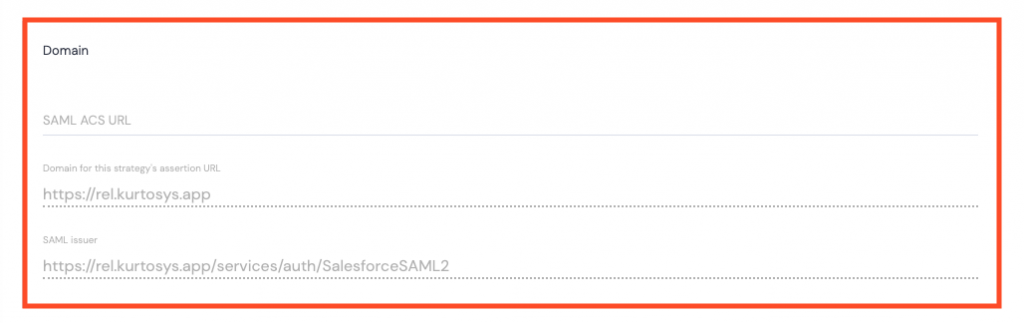
All Domain information is automatically populated.
Authentication
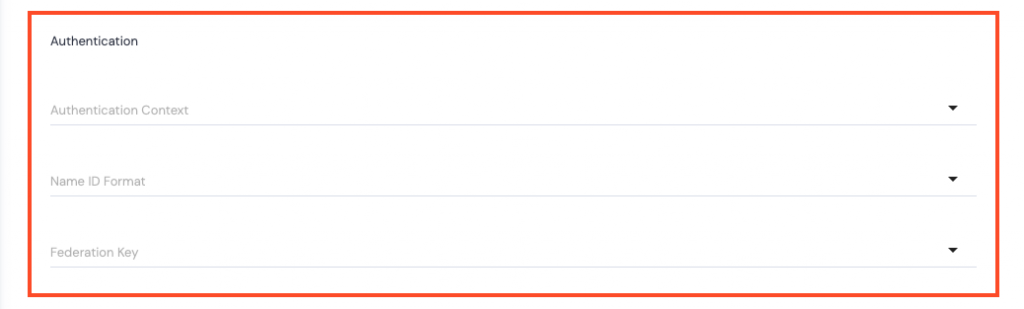
- Authentication Context – use the dropdown arrow to select one of the following:
- urn:oasis:names:tc:SAML:2.0:ac:classes:Password – Password is presented to the app over an unprotected HTTPS session.
- urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport – Password is presented to the app over a protected session.
- urn:oasis:names:tc:SAML:2.0:ac:classes:TLSClient – A client certificate, secured with the SSL/TLS transport, is presented to the app for authentication.
- urn:oasis:names:tc:SAML:2.0:ac:classes:X509 – A digital signature, where the key was validated as part of an X.509 Public Key Infrastructure, is presented to the app for authentication.
- urn:federation:authentication:windows – The user’s Windows credentials are presented to the app for authentication.
- http://schemas.microsoft.com/ws/2008/06/identity/authenticationmethod/windows – The user’s Windows
domain\usercredentials are presented to the app for authentication. - urn:oasis:names:tc:SAML:2.0:ac:classes:Kerberos – A password to a local authentication authority is used to obtain a Kerberos ticket, which is then presented to the app for authentication.
- Name ID Format – use the dropdown arrow to specify the Name ID Format that should come from the Identity Provider:
- urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress – the app expects the Name ID in an email address format.
- urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified – the format is specified at the identity provider level and the app parses the incoming Name ID Format.
- urn:oasis:names:tc:SAML:2.0:nameid-format:persistent – a persistent identifier is used for authentication to the app.
- urn:oasis:names:tc:SAML:2.0:nameid-format:transient – a random string of characters, that isn’t fixed for a user, is used for authentication to the app.
- Federation Key – use the dropdown arrow to select from the following options:
- Email – the users email address will be used to authenticate their login.
- ExternalUserIdentifier – the External User Identifier that can be viewed in a user’s User Profile section of the Kurtosys app is used to authenticate their login.
- UserName – the user’s Kurtosys app username is used to authenticate login.
Click Save. A green successful task pop up bar will display across the bottom of the screen.
Using SSO as the only Sign-On Method to log into the Kurtosys App
If you have multiple login strategies for a Kurtosys App Client Instance, all login strategies will be available on the Login page. To enforce the use of a specific strategy, following the following process:
- Click the Settings cog to access the System Administration tools.

- Click the Authentication tab to view the login strategies available.
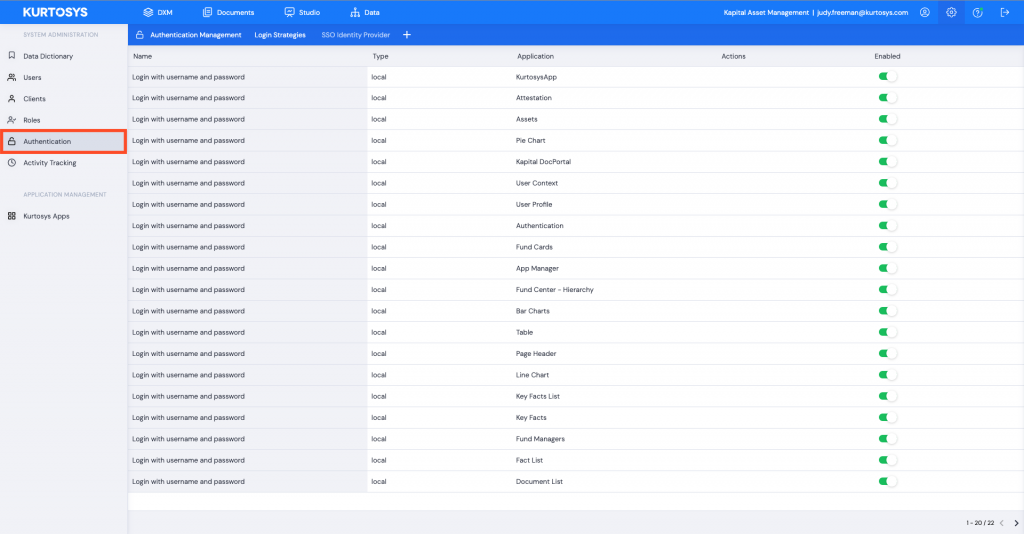
- Toggle off the login strategy you don’t want the users to access, e.g. the Kurtosys App strategy.
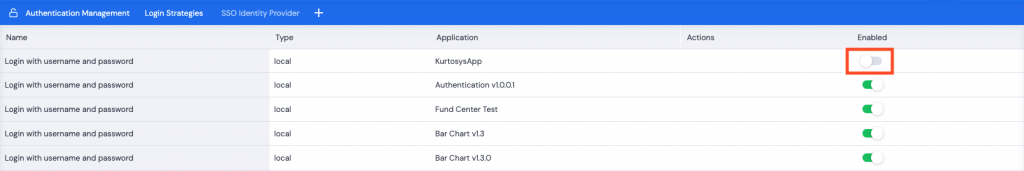
Note: You must have another strategy enabled for the application before disabling the strategy that is no longer required.
